Identity is the new perimeter. Most enterprises know this in theory, yet still struggle with Identity and Access Management (IAM) challenges in practice.
Between multi-cloud, SaaS sprawl, hybrid work, compliance pressure, and talent gaps, IAM for enterprises has become a high-stakes problem that touches revenue, risk, and reputation.
If you are a CISO, CIO, or CTO, you already feel the pain. Your teams are trying to keep up with access requests, audits, and incident tickets, while still expected to “modernize IAM” and “enable zero trust” without disrupting the business.
This article breaks down the most common enterprise IAM challenges, why they exist, and what IAM experts like miniOrange do differently to solve them in a pragmatic and repeatable way.
Why IAM Challenges Exist?
Identity and Access Management (IAM) is a cybersecurity solution, comprising policies, processes, and technology, which ensures only authorized users have access to the right resources for the right reasons.
With so many aspects to IAM, it becomes complicated for enterprises to plan, strategize, and execute, making it challenging.
Some of the reasons for the complexity are:
- Years of mergers and acquisitions have introduced multiple identity sources and directories.
- Legacy applications that never anticipated modern Identity Federation or SSO.
- Compliance frameworks are growing stricter and more prescriptive.
- Limited in-house IAM talent and constant turnover in security teams.
- Emergence of machine identities and ways to secure them.
The problem is not simply “we need a new IAM platform.” The problem is that identity has grown organically across enterprises, while the risk surface and regulatory obligations have grown exponentially.
Modern IAM for enterprises has to reconcile decades of legacy decisions with today’s need for zero trust, cloud-first architectures, and frictionless digital experiences.
Common IAM Challenges Faced by Enterprises
We’ve put together IAM challenges that organizations are facing, or may face while trying to scale and counter cybersecurity risks.
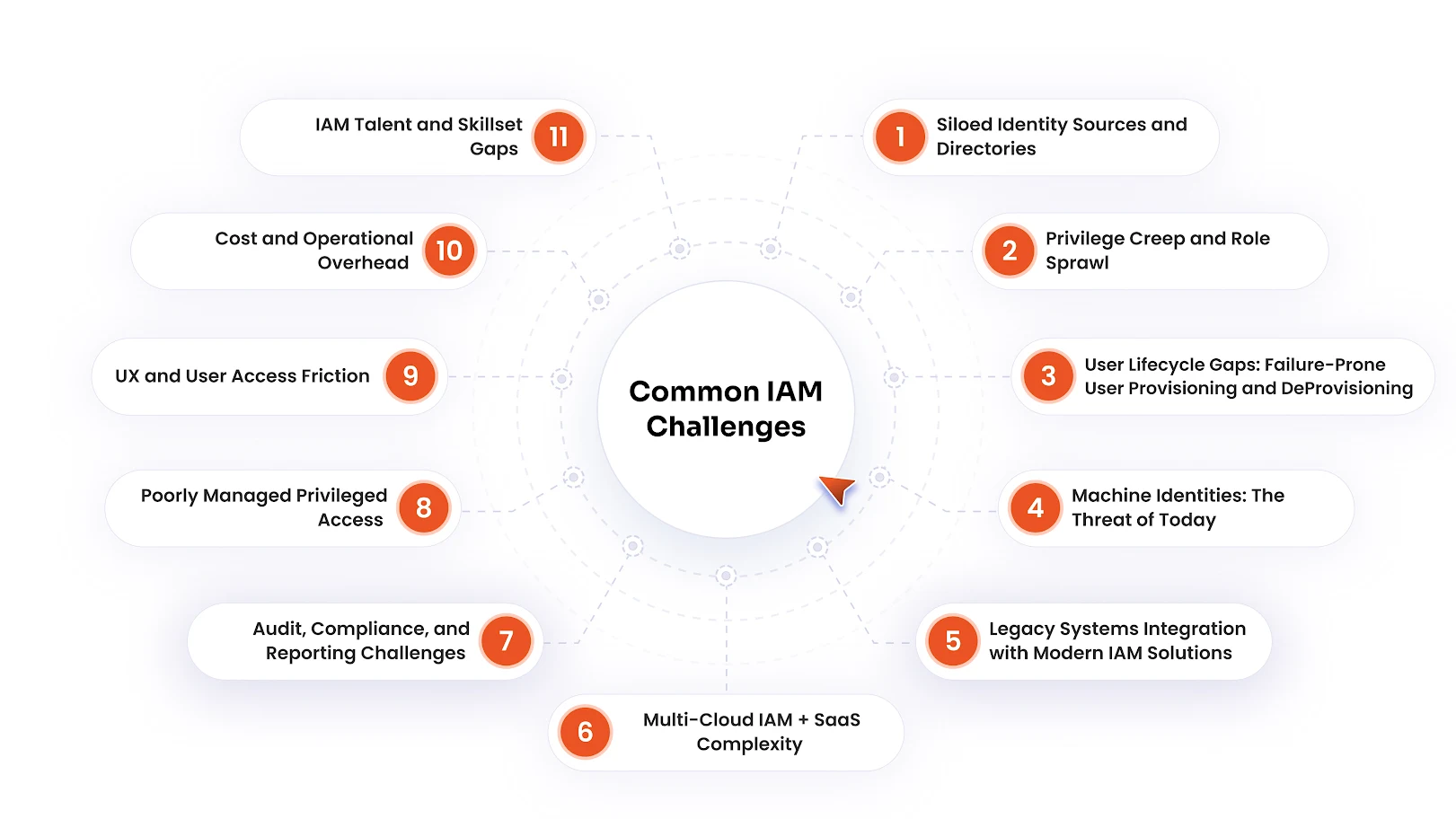
1. Siloed Identity Sources and Directories
Many enterprises maintain multiple identity stores, for instance, Active Directory for on-prem users, Azure AD or other IDaaS (Identity as a Service) for cloud apps, local credentials stored inside line-of-business apps, and separate directories for contractors and partners.
This fragmentation creates:
- Inconsistent access policies across environments.
- Multiple credentials per user, increasing password fatigue and risk.
- More chances of data breaches.
- Confusion across enterprises on ‘who has access to what resources.’
Solution: Opt for identity federation and Sign-Sign-On (SSO) solution, where siloed systems can be linked together. So, users can gain access to multiple apps with just one set of credentials. This improves user experience and security.
2. Privilege Creep and Role Sprawl
Over time, users accumulate access they no longer need. Promotion, internal moves, project-based assignments, and emergency access all add up. This leads to privilege creep.
Consequences of privilege creep are:
- Increase in chances of insider threats.
- Rise in the attack surface for the cybercriminals.
- Difficulty in implementing least privilege and zero trust principles.
For admins, this looks like manually tweaking roles and groups to “just make it work,” which creates role sprawl that becomes impossible to maintain.
Solution: Go for approaches that manage user access, such as Role-Based Access Control (RBAC), Attribute-Based Access Control (ABAC), and Policy-Based Access Control (PBAC).
3. User Lifecycle Gaps: Failure-Prone User Provisioning and De-Provisioning
The Joiner-Mover-Leaver (JML) or the user lifecycle process is the backbone of effective identity and access management, yet it remains one of the most stubborn enterprise IAM challenges.
For example, new hires (joiners) wait days for access, employees switching roles (movers) drag old permissions into new jobs, and departing staff (leavers) retain credentials long after their last day.
User lifecycle creates gaps and security risks, such as:
- Delay in onboarding/provisioning, resulting in excessive helpdesk load and loss of productivity for the employee.
- Untimely offboarding leads to zombie accounts, insider threats, and compliance violations.
- Accumulation of roles or unclear entitlement/ownership changes, resulting in privilege creep.
Solution: Automate the user provisioning and deprovisioning process, along with dynamic role updates. Also, opt for a Just-in-Time (JIT) solution for granting temporary access that expires after a certain time, reducing threats.
4. Machine Identities: The Threat of Today
Most enterprises treat machine identities as an afterthought. As organizations adopt microservices, APIs, containers, and automation, machine identities multiply faster than human identities. They operate with no oversight, too many privileges, and weak credentials, posing a serious IAM challenge and security risk.
Solution: Always give limited permissions to machine identities via the Principle of Least Privilege (PoLP). Regularly conduct audits of the permissions and activities of the machine identities to curb security risks.
5. Legacy Systems Integration with Modern IAM Solutions
Many mission-critical applications were built long before modern protocols like SAML, OAuth, or OpenID Connect existed.
These legacy systems:
- Do not support modern SSO or Identity Federation natively.
- Require custom connectors or proxies to integrate with IAM platforms.
- Often hold their own local users and passwords.
From a business standpoint, rewriting or replacing these systems is expensive and risky. From a security standpoint, they become long-term anchors that prevent IAM modernization.
Solution: Utilize access gateways, LDAP proxy, or ID federation services to expand the IAM reach to legacy apps, and gradually introduce IAM modernization without disrupting the operations of legacy apps.
6. Multi-Cloud IAM + SaaS Complexity
Enterprises rarely use a single cloud. More commonly, they have a mix of AWS, Azure, and GCP for data and analytics, and dozens or hundreds of SaaS applications purchased by different teams.
IAM in a single cloud is hard enough. IAM multi-cloud is even more complex when each provider has its own identity, siloed directories, conflicting policies, and a lack of clarity on who is working on what across the cloud. This poses an IAM challenge for the enterprises.
Key challenges include:
- Inconsistent access models across clouds.
- Difficulty implementing a unified cloud identity structure.
- Risky local admin accounts and ad hoc configurations in SaaS tenants.
Solution: Opt for Cloud Infrastructure Entitlement Management (CIEM) to map permissions of every user and machine identity. Also, instead of handling users across multiple Identity Providers (IdPs) like AWS, Google, or Azure, go for a centralized one.
7. Audit, Compliance, and Reporting Challenges
Audit, compliance, and reporting challenges in IAM arise when identities, access policies, and logs are scattered across multiple systems, making it hard to prove “who had access to what, when, and why” for SOC2, SOX, HIPAA, GDPR, PCI-DSS, and ISO 27001 audits.
Solution: Implement centralized IAM with built-in governance so all authentication, authorization, and admin events are logged in one place, and access reviews are automated and policy-driven.
8. Poorly Managed Privileged Access
Privileged accounts include domain admins, cloud root accounts, database owners, DevOps and SRE users, and powerful service accounts. If these are over-privileged, shared, or poorly monitored, a single compromise can lead to a full environment takeover. This creates a major IAM challenge and security risk.
Poorly managed privileges look like:
- Shared admin accounts with generic usernames and passwords that are passed around in chats or documents.
- Always-on admin rights are granted “just in case” and never revoked, creating excessive privileges.
- Orphaned privileged accounts for ex-employees, vendors, or old projects that nobody actively owns.
- No consistent MFA, logging, or monitoring on high-risk admin actions or sessions.
Solution: Make use of Zero Standing Privilege (ZSP), as it is a security approach where no user account (human or machine) has permanent access rights.
So, instead of always-on access, permissions/privileges are granted only when required and revoked after the task is finished. Think of ZSP as the ultimate evolution of PoLP.
9. UX and User Access Friction
If the IAM system UX is difficult to navigate, then users are bound to look for shortcuts that bypass safeguards entirely. This turns a simple usability friction into a serious IAM challenge.
Reasons for the friction are:
- Inconsistent login flows or SSO
- Frequent lockouts
- Multiple passwords and MFA fatigue
- Poor mobile UX
Solution: Leverage adaptive authentication for low-risk users and shift to passwordless authentication methods (passkeys and biometrics). Ensure better SSO for systems and work on the mobile UX.
10. Cost and Operational Overhead
IAM can quietly become one of the most expensive parts of your security stack when it grows without a plan. Many teams only realize this when budgets get tight or audits start asking hard questions.
Challenges with an unplanned IAM strategy are:
- Manual tickets for access requests
- IAM projects fail because of operational complexity
- Multiple vendors for Identity Federation, SSO, MFA, and PAM that don’t fully talk to each other.
- Overlapping licenses and features that are bought but barely used.
Solution: Rationalize licenses by phasing out duplicate tools and consolidating on the capabilities you actually use. Furthermore, move toward a unified IAM platform that covers SSO, MFA, PAM, and lifecycle management in one place.
11. IAM Talent and Skillset Gaps
IAM is specialized: you need people who understand protocols (SAML, OAuth, OIDC), cloud IAM models, RBAC design, compliance requirements, and real-world implementation tradeoffs.
Most enterprises are short on this kind of talent. The result is:
- Stalled projects
- Brittle custom integrations
- Dependence on a few overworked specialists.
- Continuity and resilience risks for the C-suite are not a staffing issue.
Solution: Partner with IAM experts (like miniOrange) who bring reference architectures, accelerators, and managed services rather than starting from scratch. Also, choose IAM platforms that reduce custom code and offer defaults aligned with zero trust and compliance.
How IAM Experts Solve These Enterprise Challenges?
IAM modernization is not just about buying a platform. It is about adopting IAM best practices, aligning with zero trust, and simplifying the experience for users, security teams, and auditors.
Here is how IAM experts approach these challenges:
- Identity Federation and SSO: Give users one secure login for all apps while centralizing control for security teams.
- Automated User Lifecycle Management: Automatically grant, update, and remove access as people join, move, or leave the organization.
- Unified Identity Management: Manage all human and machine identities from a single source across on-prem and cloud.
- Implementing Privileged Access: Protect high-risk admin accounts with least privilege, approvals, and strong oversight.
- Following Zero Trust Architecture: Continuously verify every user and device instead of trusting the network by default.
- Implement MFA and Passwordless Authentication: Add strong, user-friendly authentication that goes beyond passwords to block account takeover, data breaches, credential stuffing, and other types of threats.
- Adopting Continuous Monitoring, Reviews, and Access Policies: Keep access clean over time with ongoing checks, alerts, and regular access reviews.
- Solving Multi-Cloud IAM Complexity: Apply consistent identity, access, and governance policies across all your cloud platforms and SaaS apps.
All of these will give enterprises a consistent and strong security posture, and they will be able to manage identity access easily.
Conclusion
Enterprise IAM challenges are not going away. In fact, as AI, automation, and multi-cloud adoption accelerate, identity will only become more central to your security strategy and compliance posture.
Executives who treat IAM as a strategic business initiative rather than a technical afterthought see better outcomes, such as:
- Lower breach probability and impact.
- Smoother audits across SOC2, SOX, HIPAA, GDPR, PCI-DSS, and ISO 27001.
- Better user experience and productivity.
- A cleaner path to zero trust and cloud-first strategies.
Working with IAM experts like miniOrange enables you to unify identities, modernize your stack, implement strong controls such as SSO, MFA, PAM, and RBAC, and tame the complexity of IAM for enterprises in a way that aligns with business goals.
Elevate Security with the miniOrange IAM Suite
miniOrange IAM suite offers products for both employees and customers across cloud and on-premise deployment modes.
Our core IAM offerings revolve around SSO, MFA, Adaptive/Risk-Based Authentication, PAM, user lifecycle management, and passwordless logins.
To know more about our IAM product suite, get in touch with us for a demo session, or sign up for a 30-day free trial.
FAQs
What are the four pillars of IAM?
The four pillars of IAM are authorization, authentication, governance, and user management. All of them together make sure that only the right people have access to the resources, at the right time, and for the right reasons.
What are the IAM challenges in cloud computing?
Key challenges are shadow IT, configuration errors, compliance, over-privileged accounts, and handling the lifecycle of identities.
How can enterprises manage privileged access more effectively?
Enterprises can improve Privileged Access Management (PAM) by implementing just-in-time elevation, strong MFA, session monitoring, and regular reviews of privileged roles. Integrating PAM with broader IAM policies ensures consistent governance across on-prem and cloud environments.



Leave a Comment