Credential stuffing attacks have become one of the most common, yet underestimated, cybersecurity threats facing businesses today. Even with strong firewalls and the latest endpoint protection, organizations still lose millions every year to stolen login credentials reused across accounts.
What’s worse, these attacks often stay undetected until real damage occurs, which includes data breaches, customer account takeovers, and regulatory penalties.
In this blog, we’ll unpack what credential stuffing really is, why it’s so dangerous in modern cybersecurity, how attackers execute these campaigns, and, most importantly, the proven strategies, including Multi-Factor Authentication (MFA) methods offered by miniOrange, to prevent credential stuffing attacks effectively.
What is Credential Stuffing in Cybersecurity?
Credential stuffing is a type of cybersecurity attack where threat entities use stolen usernames and passwords, often acquired from previous data breaches, to gain unauthorized access to a system.
The attack is based on the assumption that users reuse their credentials across multiple platforms. For instance, if your company’s employees reused their LinkedIn password for your internal HR portal. If that LinkedIn password is ever exposed in a breach, attackers can easily “stuff” those credentials into your HR system’s login page, hoping for a match.
While basic credential stuffing attacks rely on simple automation, enterprise-level threats are far more sophisticated. Attackers now deploy massive botnets that utilize proxy rotation and device fingerprint evasion to mask their identity. Additionally, to traditional firewalls and basic security tools, the malicious activity looks like normal traffic, allowing it to bypass rate limits and IP bans undetected.
From a cybersecurity standpoint, credential stuffing exploits one of the weakest links in any system: human password habits. The more platforms a user engages with, the higher the probability that their credentials are reused somewhere else.
What is the Impact of Credential Stuffing Attack?
While many think of credential stuffing as a minor threat, the impact on an organization can be immense.
Some of the typical repercussions include:
1. Financial Frauds and Chargebacks
Businesses face direct financial losses from fraud, as attackers abuse stolen credentials to make unauthorized purchases, access premium services, or steal sensitive data. This is followed by a wave of chargebacks from banks and credit card processors, which not only drains revenue but can also damage merchant standing and increase processing fees.
2. Brand Reputation Damage
Customer trust takes a severe hit when accounts are compromised. Negative media coverage about poor password or account protection practices can permanently erode brand equity.
3. Operational Disruption
Detection systems, password resets, and forensic audits require significant IT and security resources. During remediation, day-to-day business operations can slow down.
4. Compliance and Legal Risks
Violations of data protection regulations such as GDPR, CCPA, or HIPAA can lead to hefty fines and long-term reputational damage for businesses.
A single credential stuffing attack can have a snowball effect, from a few breached accounts to a widespread data compromise. So, it is necessary to curb it beforehand.
5. Surging SOC and IR Workload
Every wave of stuffing attacks triggers thousands of alerts. This floods the Security Operations Center (SOC), forcing analysts to waste hours sifting through noise rather than focusing on genuine threats.
When a breach is successful, the Incident Response (IR) costs skyrocket as teams work to contain the damage and reset thousands of users.
Credential Stuffing vs. Brute Force vs. Password Spraying Attacks
We’ve highlighted key differences between the three:
- Credential Stuffing: Relies on leaked credential lists from previous breaches. Attackers try known username-password pairs across multiple platforms until they find valid ones to gain unauthorized access to the systems. The success rate is high when users reuse their credentials for multiple platforms.
- Brute Force Attacks: Brute force attacks involve systematically guessing passwords by trying every possible combination for a given target account. Attackers use automation to try every possible combination until the right one is found. This attack is time-consuming and computationally intensive; too many attempts may lead to rate-limiting or lockouts.
- Password Spraying: Instead of targeting one account with many passwords, attackers try one common password (like 123456789) across many accounts to avoid lockouts. This attack is based on the assumption that several users use weak or common passwords.
Understanding these nuances helps organizations deploy the right security measures against each type of threat.
How do Credential Stuffing Attacks Work?
Credential stuffing attacks follow a structured pipeline designed for scale and automation:
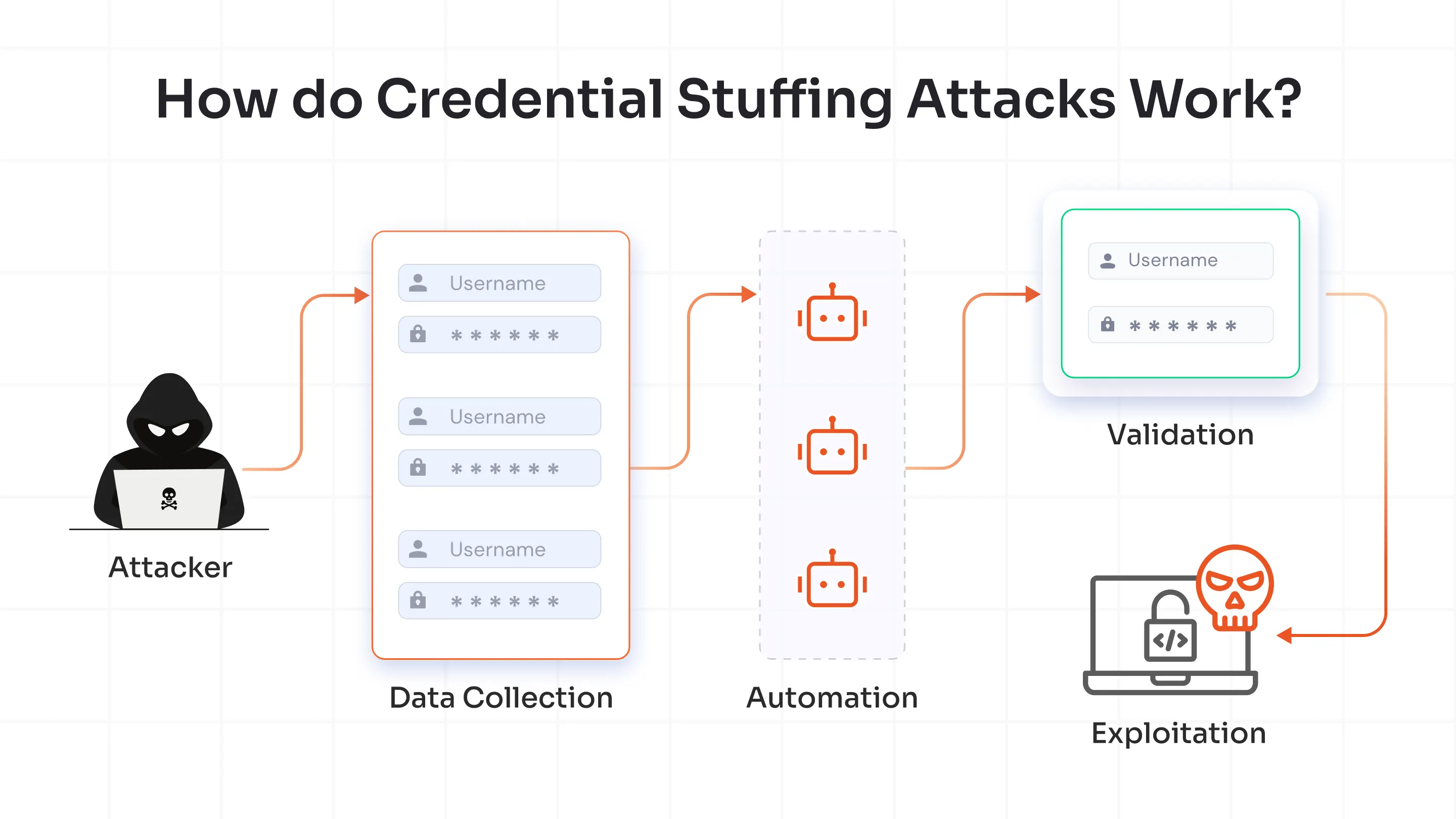
1. Data Collection: Attackers gather stolen username-password pairs from the dark web, phishing campaigns, or previous breaches.
2. Automation: Using tools like Sentry MBA, Snipr, or custom Python scripts, they automate login attempts across multiple target websites or APIs.
3. Validation: They monitor which credential combinations succeed, often using proxy networks or botnets to mask their identity.
4. Exploitation: Valid credentials are then used to access personal data, financial accounts, or internal systems, sometimes even resold to other cybercriminals.
Example Scenario
If your company’s customer portal sees an unusual rise in failed login attempts with legitimate email usernames, there’s a good chance it’s under a credential stuffing attack.
Security teams often identify credential stuffing through these distinct patterns:
- High Login Velocity from Distributed IPs: Instead of a single IP hammering the server, you see thousands of login attempts spread across hundreds of different IP addresses within seconds, bypassing standard rate limits.
- Abnormal User-Agents and Fingerprints: The traffic shows requests coming from "headless" browsers or outdated/mismatched User-Agent strings that don’t align with real customer devices.
- High Failure Rate and Scattered Geo: You notice an overwhelming number of failed logins originating from unexpected geographic locations where you have no customer base, or impossible travel scenarios.
- Password Spraying Overlap: In some cases, you might see the same password being tested across many different accounts simultaneously.
Because these attacks mimic normal user behavior, traditional firewalls or IP filtering alone often fail to detect them.
Real-World Examples of Credential Stuffing Attacks
Credential stuffing isn't theoretical; high-profile incidents have proven how damaging it can be.
1. Passwords Exposed Online
In late January 2026, cybersecurity experts discovered a massive, publicly exposed database containing 149 million usernames and passwords, sending shockwaves through the digital ecosystem.
The database reportedly included credentials tied to a variety of online services, including email platforms, social networks, banking portals, streaming services, and more. These unsecured credentials have the potential to be used for a credential stuffing attack.
2. North Face and Cartier Customer Data Stolen
BBC reports that fashion brand The North Face and luxury jeweller Cartier have had customer data stolen in recent cyber attacks, making them the latest major retailers to be hit. The breaches involve hackers accessing customer accounts, with stolen information including names, contact details, and order histories, though payment card data is said to be unaffected.
The incidents, which came to light in early June 2025, have prompted warnings for shoppers not to reuse passwords across multiple sites and to update their login details immediately. Security experts say the attacks are likely linked to credential stuffing, where criminals use previously leaked usernames and passwords to break into online accounts.
3. Major Breach: 16 Billion Login Credentials Exposed
In June 2025, cybersecurity researchers revealed that a record 16 billion login credentials had been exposed online in what is believed to be the world’s largest password leak to date.
The data, compiled from at least 30 exposed datasets, includes usernames and passwords for major platforms such as Apple, Google, Facebook, GitHub, Telegram, VPNs, and even some government services.
Authorities and security specialists warn that the leak could fuel large-scale credential stuffing, phishing, identity theft, and account takeover attacks worldwide if users and organizations do not act quickly.
What are the Preventive Measures of Credential Stuffing?
Building resilience against credential stuffing requires a layered approach combining detection, prevention, inclusion of MFA methods, and intelligent user authentication. Let’s break down the most effective measures.
1. CAPTCHA
CAPTCHA needs users to prove that they’re human, and it significantly reduces the chances of a credential stuffing attack.
While simple, they effectively reduce low-level bot traffic. However, attackers can bypass basic CAPTCHA, so it’s best used alongside more advanced solutions, for instance, biometric authentication or passkeys.
2. Multi-Factor Authentication (MFA)
A Multi-Factor Authentication (MFA) solution adds an extra layer of protection beyond just passwords, preventing credential stuffing attacks. By enabling MFA software, users can authenticate themselves with something they know (PIN or password), something they have (hardware token), or something they are (fingerprint scanning or iris scan).
3. Monitoring and Anomaly Detection
Security teams must continually monitor for unusual login patterns such as multiple failed attempts from different IPs or logins from unknown geolocations. They also need to detect unusual session durations.
Furthermore, AI-driven login anomaly detection tools can identify and block credential stuffing attempts in real-time by recognizing non-human patterns.
4. WAAP (Web Application and API Protection)
A WAAP platform provides comprehensive protection for both applications and APIs by combining WAF, bot management, and DDoS mitigation.
While a traditional Web Application Firewall (WAF) can spot and block unusual login attempts using rate limiting and IP blocking, WAF alone often fails to stop sophisticated credential stuffing. This is because modern attackers use residential proxies, real browser fingerprints, and "low-and-slow" attack patterns to fly under the radar of standard threshold-based detection.
A complete WAAP solution goes beyond simple blocking to analyze intent and behavior, ensuring that even stealthy automated tools are neutralized before they compromise accounts.
5. IP Blacklisting
Blocking IP addresses linked to suspicious activities helps slow down automated attacks. While attackers rotate proxies, dynamic IP reputation lists can help block known malicious IP ranges.
Before blocking a suspected anomalous IP, compare it against the user’s recent login history. Auditing past telemetry helps filter out false positives and ensures legitimate users aren’t locked out by mistake.
6. Rate Limiting
Rate limiting governs how many login attempts can occur within a given timeframe. This helps prevent attackers from rapidly testing multiple credentials and reduces server stress caused by bot-driven traffic spikes.
7. Leverage Behavioral Biometrics
Behavioral biometrics analyzes how a user interacts with a system, such as keystroke speed, mouse movement, typing cadence, rather than just what credentials they use. It’s almost impossible for a bot to replicate these micro-patterns, making it a strong anti-bot layer.
8. Block Headless Browsers
Headless browsers are popular among attackers because they replicate real browser behavior without visual rendering. Tools can now detect and block these environments by checking for missing browser fingerprints or inconsistent JavaScript execution.
9. Passwordless Authentication
Passwordless authentication replaces passwords with secure mechanisms such as biometrics, hardware tokens, or passkeys. It not only prevents credential stuffing entirely but also simplifies the user experience and reduces IT support overhead.
How miniOrange Solutions Help to Defend Against Credential Stuffing?
miniOrange, a global leader in Identity and Access Management (IAM), provides a range of solutions that directly address credential stuffing threats for enterprises and SMBs alike.
From biometrics to FIDO2 tokens, miniOrange supports modern passwordless login flows that eliminate the need for passwords, closing the door on credential reuse.
Furthermore, miniOrange’s adaptive MFA solutions dynamically adjust authentication requirements based on user behavior and risk levels. This ensures frictionless login experiences for legitimate users while blocking suspicious activity.
Also, MFA methods such as hardware tokens, grid pattern matching, passkeys, authenticator apps, and more can help evade credential stuffing.
For CIOs and security architects looking to balance usability and security, miniOrange provides flexible MFA options for end-to-end protection against credential stuffing and related attacks.
To know more, just connect with us for a demo session with our experts or sign up for a 30-day free trial.
FAQs
What is MFA?
Multi-Factor Authentication (MFA) is a security process that requires two or more forms of verification before granting access. This may include something you know (password), something you have (device or token), or something you are (biometric).
How can businesses detect a credential stuffing attack in progress?
Typical signs include sudden spikes in failed login attempts, logins from unusual locations or devices, and many login attempts using known email formats. Security teams can use monitoring, risk-based authentication, and anomaly detection to flag and block these patterns.
What role do bots play in credential stuffing attacks?
Bots automate the process of testing millions of username and password combinations across multiple applications. They help attackers scale their operations, rotate IPs, and mimic human behavior to bypass basic security controls.





Leave a Comment